|
Cloud computing allows users to build a virtual platform that facilitates storage, service, and infrastructure over virtual clouds. Additionally, cloud computing increases the efficiency of the end-user and reduces the cost to create physical servers. Such a cloud computing facility has three core issues in implementation over diverse demographics, platforms, and servers:
1. Why do we face compliance issues in Cloud computing? Elasticity, scalability, global access, low entry cost and flexible billing, made cloud platform, a sophisticated source of data storage for many users, such a massive demand for cloud storage generates new compliance issues like government regulations, legal amendments, etc. Sometimes, government regulations also play a crucial role in compliance issues across cloud systems. Regulations are usually tedious and redundant. So, it is incredibly difficult to understand and compile different methods with each other. Compliance issues and recommendations for cloud computing
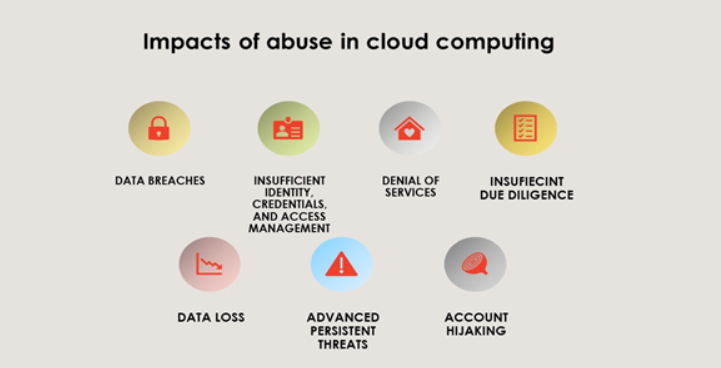
2. What is abuse in cloud computing? The term abuse in cloud computing generally refers to the practice of illegal activities by using cloud resources. Abuse may happen either by the person who is a legitimate cloud service provider or someone who has occupied control of the customer resources. Currently, IaaS is the most abused platform over other online platforms. Some of the abusing activities that usually happen to IaaS providers:
Prevention of Abuse in Cloud computing Technical measures
3. How security and privacy issues shrunk cloud computing? Cloud computing helps in accessing all the digital files like emails, documents, and sensitive information through their servers from an unknown location, creating a path for privacy and security breach across the platform. So, cloud computing users should consider the following issues to overcome security breaches over the platform.
The 'only' recommendation to safeguard security concerns in cloud computing is to frame the cloud platform into four custom layers: Virtual Network monitor layer, Cloud data layer, Cloud storage layer and Virtual machine layer. Conclusion: Overall, cloud computing is an industry where a lot of improvements are evolving, eventually leads to certain vernacular issues like compliance, Abuse and Security. And hence, it is more crucial than ever that we take the right measures since the beginning to avoid complications in the future! To know more about Cloud or to explore Cloud Computing services with H-Town Technologies, visit: https://www.htown-tech.com/cloud-computing.html
7 Comments
Ryan Hughes
29/3/2021 15:25:08
Crisp and to the point!
Reply
14/4/2021 05:41:32
The blog is addressing on the top 3 challange in the cloud computing with the recommendation in detail. Such content must be made more and more available. Thank you for this article! This is really very informative. I love this article, thanks for producing such great contents. I love your posts always.
Reply
2/2/2023 01:42:40
Thanks for your information. i am read your article i am very impressive.
Reply
Nagaraj
31/3/2023 07:09:35
Great website, thanks for sharing https://revaalolabs.com/post/top-10-cloud-computing-challenges-in-2020 Please visit our website
Reply
Thank you for sharing this relevant and useful information. this is great and important information, If you want to bring your app ideas into action, then check out our services at <a href="https://www.openteqgroup.com/services/cloud-services"> top cloud services company in india </a>,<a href="https://www.openteqgroup.com/services/cloud-services"> top cloud backup solutions company in india </a>
Reply
12/10/2023 02:46:15
Htown Tech's blog on the top challenges in cloud computing offers valuable insights into the potential pitfalls and how to address them. Cloud computing is transformative, but it comes with its set of challenges, which this article adeptly addresses. The recommendations provided are practical and useful for organizations navigating the cloud landscape. It's a must-read for those considering or already using cloud services.
Reply
Leave a Reply. |
Tech TalksStay up to date with the tech world and the latest trends in the industry. Archives
August 2021
Categories
All
|
|
H-Town Technologies Inc. is designed to
provide continuous and comprehensive support to all our clients in IT Consulting, Development and Managing their day-to- day business operations in the IT sector. |
|
COPYRIGHT © 2020. H-TOWN TECHNOLOGIES INC. ALL RIGHTS RESERVED.



 RSS Feed
RSS Feed
